Protection for AI Intellectual Property
Run your models on devices you don't fully trust
without having to worry about theft or leaks
 Deploy Anywhere
Deploy Anywhere
The model is contained in an eCora encrypted virtual machine which
supports edge and offline use
 Prevent Theft and Leaks
Prevent Theft and Leaks
Remains encrypted even in use so neither the user, cloud
provider nor eCora can see inside the container
 Keep Data Private
Keep Data Private
All Data sent to and received from the container always remains
encrypted and can only be seen by the user
Product
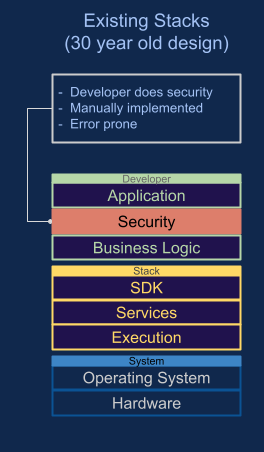
The eCora Secure Application Stack uses technology innovations
in cybersecurity, edge computing, and confidential computing
Encrypted Container
Encrypt existing applications or native Wasm modules into a
secure container. Confidential Computing technology is
used to ensure the application remains encrypted while executing

Policies and Rules
Define policies and rules which are checked before and after every
execution request. These can be used to control anything such
as access rights, limits, quotas and even calculate billing

Easy Deployment
Build the application as usual using your existing tools and then use
eCora to quickly encrypt it into a container. This eCora container
can then be deployed anywhere on the customer's IT estate
For AI Developer/Vendor
Do you have customers who want to install your model in their IT
estate? Are you concerned about your valuable model IP being
stolen?
Ship your model to your customers as an API enabled encrypted
container with policies and rules to control access
For AI User/Customer
Are policies or regulations stopping you from using external AI
SaaS services? Are you concerned that your data may leak if
you use the cloud?
Deploy a vendor's encrypted AI model into your IT estate
knowing your data cannot be seen by anyone else
Solution
Healthcare
Maintain patient data confidentiality
Healthcare AI usually trains models on special data sets that are
either anonymised or synthesised to protect patient
confidentiality. Healthcare organisations struggle to keep
these data sets up to date and relevant
eCora allows healthcare AI to send real data without the risk of
leakage
Cybersecurity
Keep network traffic inside the perimeter
Anomaly and intrusion detection software is increasingly using AI to
cope with the variety of cyber attacks that occur today.
Enterprises however, don't want to send their internal network
packets and logs to external services
eCora allows vendors to securely deploy their encrypted IP on
customer premises
Financial Services
Safely aggregate transaction data
Fraud and money laundering AI services are heavily used today but
because of regulations, PII must be stripped out which means they
cannot correlate information across different companies to better
detect illegal activities.
eCora allows encrypted data sharing where no-one can see the real
data
Manufacturing
Confidential computing AI on the edge
Advanced manufacturing are using AI for predictive maintenance and
process optimisation however, many want edge computing capabilities
because their factories are air-gapped to protect their process
secrets and data security
eCora uses a decentralised edge architecture that works
offline
Technology
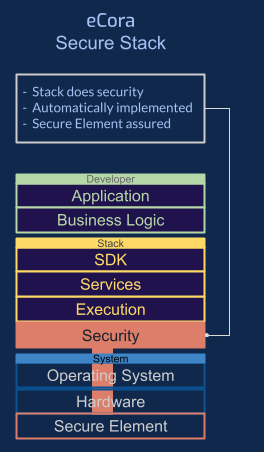
eCora Secure Application Stack
 "Security as a forethought, not an afterthought"
"Security as a forethought, not an afterthought"
Secure By Default Stack
Secure By Default is the successor paradigm to Secure By Design.
Our secure application stack implements this by putting security at
the base of the stack. This automatically enforces many security
and assurance controls and cannot be bypassed
The stack can containerize an existing application such as an AI
model or run natively written Wasm modules
Hardware Backed Security
Our stack goes all the way down to silicon. The stack base layer
uses encrypted enclave technology, with keys generated and retained in
secure elements (TPMs) which mean they cannot be extracted or
compromised.
Every activity that goes on in the stack must be signed by a secure
element and the stack automatically attests that all requests come
from a legitimate secure element
Decentralised Edge Computing
Edge computing is the successor paradigm to Cloud computing and has
better scalability and resilience. Our stack is written as edge
native code using Rust and Wasm.
The decentralised architecture of the stack means that the nodes in
our network we can work in offline mode
Data Centric Security
Data Centric Security is the successor paradigm to Network Centric
Security. The stack implements fine-grained Zero Trust at the
individual data record level.
Each data record object is a self-contained unit of security
containing its own keys, roles, permissions and functions
About Us
David Chan and Tom Whelan have both had long careers building large
complex systems, and in 2018 began looking at the latest advances in
the areas of security, scalability, and resilience. The aim was
to improve the security of application software stacks.
Applications are developed with security as an afterthought and even
then, the use of security is handcoded leading to mistakes.
What was needed was a software stack where security was not only
built-in to the stack, but was placed at the base layer so that it is
given the highest priority and can control the whole stack. This
Secure By Default approach would provide security controls
automatically.
Retrofitting an existing stack with a security base layer didn't work
because they are such different paradigms so the only course of action
was to develop a new stack. Along the way, new innovations were
developed such as a fast blockchain that utilises edge computing.
Eventually, in December 2020, the company eCora (eCoraDLT Limited) was
incorporated in Leicester, United Kingdom and received angel funding
in early 2021. In November 2021, eCora filed a patent on their
efficient blockchain protocol which allows lower powered devices such
as IoT and phones to run a layer one protocol.
Team

|

|

|
David Chan

CEO & Cofounder
|
Tom Whelan

CTO & Cofounder
|
Raphael Djondo

Principal Consultant
|

 Deploy Anywhere
Deploy Anywhere Prevent Theft and Leaks
Prevent Theft and Leaks
 Keep Data Private
Keep Data Private