David Chan and Tom Whelan have both had long careers building large
complex systems, and in 2018 began looking at the latest advances in
the areas of security, scalability, and resilience. The aim was
to improve the security of application software stacks.
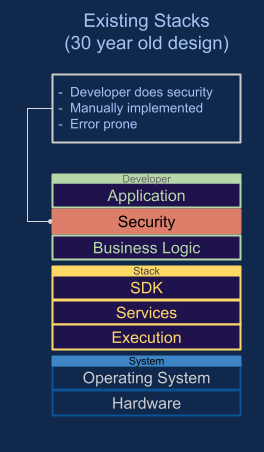
Applications are developed with security as an afterthought and even
then, the use of security is handcoded leading to mistakes.
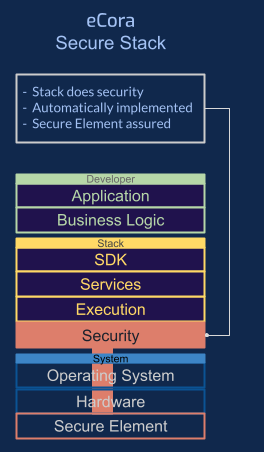
What was needed was a software stack where security was not only
built-in to the stack, but was placed at the base layer so that it is
given the highest priority and can control the whole stack. This
Secure By Default approach would provide security controls
automatically.
Retrofitting an existing stack with a security base layer didn't work
because they are such different paradigms so the only course of action
was to develop a new runtime computing stack. Along the way, new innovations were
developed such as a fast scalable blockchain that utilises edge computing.
Eventually, in December 2020, the company eCora (eCoraDLT Limited) was
incorporated in Leicester, United Kingdom and received angel funding
in early 2021. In November 2021, eCora filed a patent on their
efficient blockchain protocol which allows lower powered devices such
as IoT and phones to run a layer one protocol.